Penetration testing for WordPress and Drupal websites

Introduction
Penetration testing (pen testing) is a vital security practice for websites built on popular content management systems (CMS) like WordPress and Drupal. This process involves simulating cyberattacks to uncover potential vulnerabilities that malicious actors might exploit. Before launching any website, we conduct a comprehensive pen test to ensure robust security measures are in place. This guide provides a step-by-step walkthrough for performing penetration testing on WordPress and Drupal websites using Pentest-Tools, covering preparation, testing procedures, and post-testing actions.
Preparing for Penetration Testing
Backups
Before starting, ensure you have complete backups of your website, including databases and files. This protects against data loss during the testing phase.
Staging Environment
As a rule of thumb, conduct tests on a staging server to avoid disrupting the live website.
Legal Permissions
Obtain necessary permissions from stakeholders before testing to ensure all activities are authorized.
Using PenTest Tools
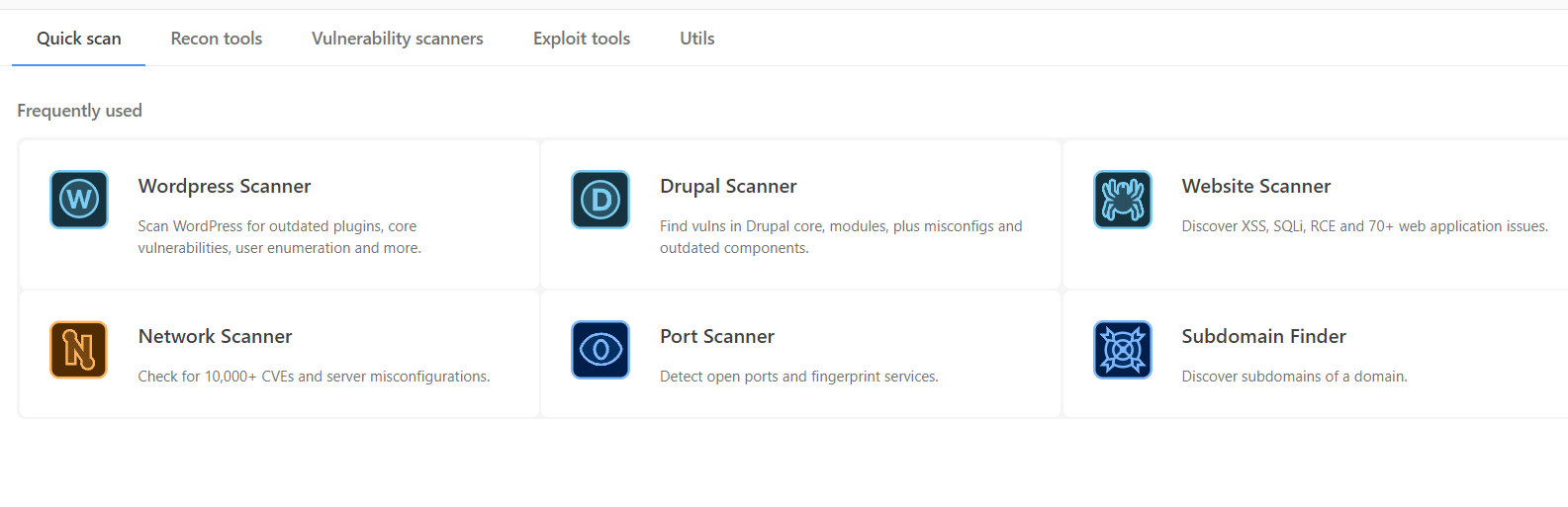
We chose to use PenTest tools for our purposes, since it provides a comprehensive suite of testing tools under one roof. Popular website scanning and penetration products like WPScan, Droopescan, Burp Suite, Metasploit, Nikto and others are used to carry out a deep security check of the website to protect from hostile attacks.
Penetration testing for WordPress websites
WordPress is the most widely used CMS platform across the globe, and it often becomes a target for hackers. Their attacks are facilitated by the high number of outdated WordPress installations and outdated plugins and themes. These old versions of WordPress components contain vulnerabilities and security weaknesses that can be exploited. These hacks can be prevented by periodically scanning the WordPress installation using a tool such as our WordPress vulnerability scanner and identifying vulnerable components.
Using WPScan, we can perform a light or deep scan to identify vulnerabilities and accordingly correct them. The tests include :
- Vulnerabilities in the core WordPress version
- Vulnerabilities in the main WordPress theme
- Interesting headers
- WP-cron enabled checks
- WordPress plugins vulnerabilities
- All WordPress theme vulnerabilities
- User enumeration & XML-RPC enabled check
- Config backups & database exports search
- TimThumbs search
Once a scan is complete, we get a summarized report about any vulnerabilities detected
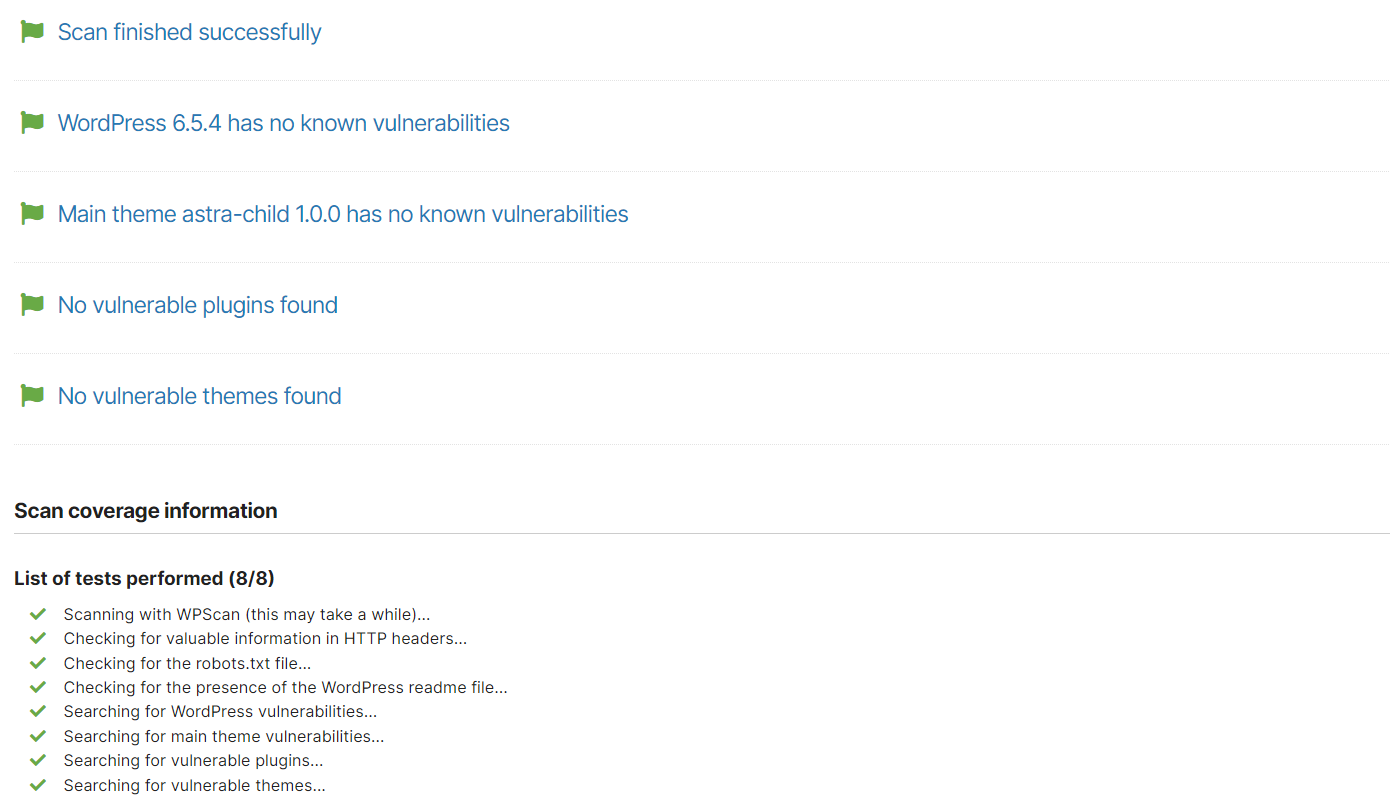
It also provides a deeper report, which our tech team can then break apart into smaller chunks to prioritize based on their risk level. You can find a sample report HERE
Penetration testing for Drupal websites
Drupal is another widely used CMS platform known for its flexibility and robustness. Hackers tend to exploit its vulnerabilities primarily due to outdated Drupal installations and outdated modules and themes. Like WordPress, these old versions of Drupal components allow hostile actors to gain access and cause disruptions in the website.
Using CMSMap or Droopescan , we can perform a thorough test of the website, which includes :
- Fingerprint the server software and technology
- Fingerprint the Drupal installation
- Find installed Drupal modules
- Find the current Drupal theme
- Search for vulnerabilities affecting the current Drupal version
- Check for directory listing
- Search for default install files
- Verify the communication security (HTTPS settings)
- Attempt user enumeration using Views module
- Attempt user discovery using Forgot Password
- Check if the login page is accessible
- Check if user registration is enabled
The scan is performed remotely, without authentication, in a black-box manner. This simulates an external attacker who tries to penetrate the target website.
Once a scan is complete, we get a summarized report about any vulnerabilities detected
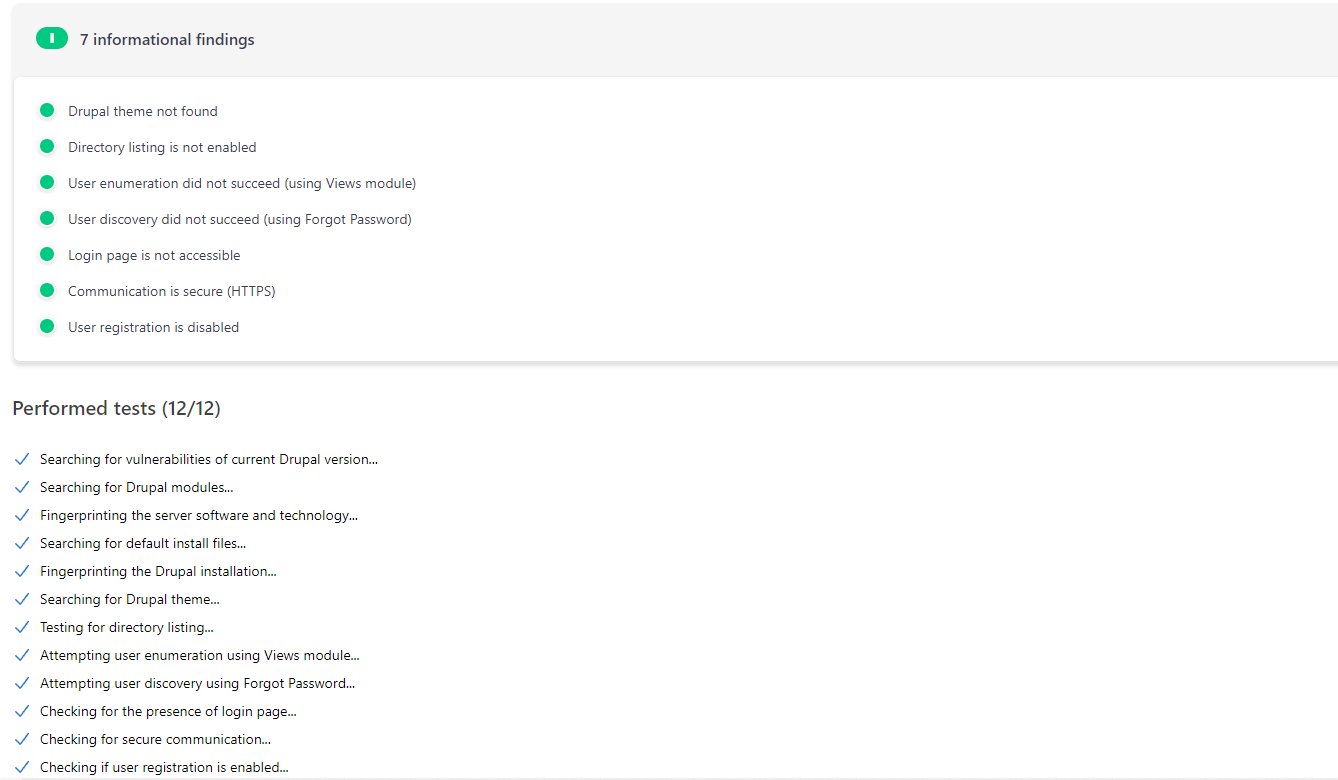
Much like the WordPress scanner, it provides a detailed report as well. You can find a sample report HERE
Post-Testing Actions
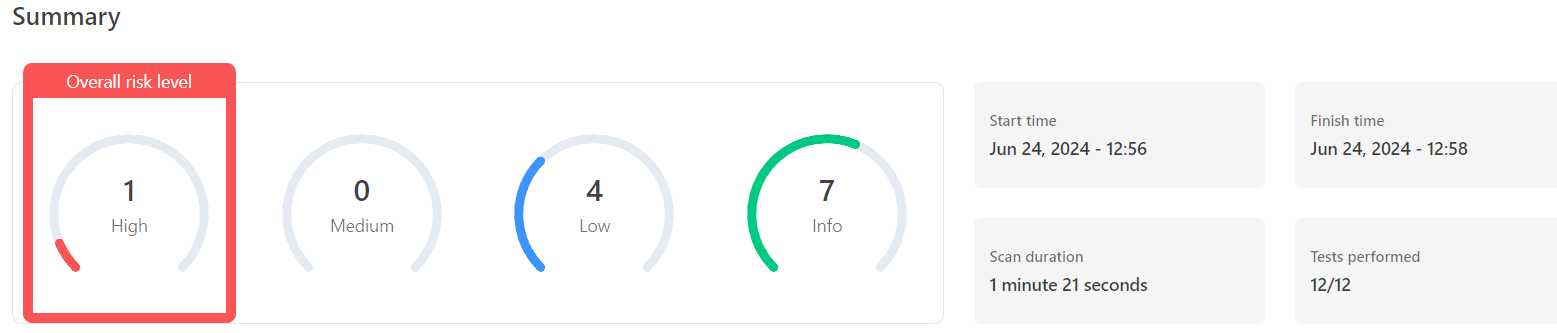
Once the results and reports have been generated. It’s important to bucket them in categories based on their level of risk, impact and urgency. The tech teams can then begin working on updating the relevant plugins , themes and core systems to their latest versions and mitigate any future incursions. In some cases, the team might need to work with the product developers to help patch out the vulnerabilities detected.
Best Practices for Ongoing Security
- Regular Updates: Keep the CMS, plugins, and themes updated.
- Strong Passwords: Enforce strong password policies.
- Two-Factor Authentication: Implement two-factor authentication for all user accounts.
- Regular Backups: Schedule regular backups of the website.
- Security Plugins: Use security plugins like Wordfence for WordPress and Drupal Security Kit for Drupal.
Conclusion
Penetration testing is an ongoing process that requires regular attention to ensure the security of WordPress and Drupal websites. By following the steps outlined in this guide and using Pentest-Tools , you can identify and mitigate vulnerabilities, thereby protecting your website from potential cyber threats.
If you enjoyed this post please follow us on LinkedIn, X and Facebook